Decentralized Threshold Key Generation & Decryption
1795

Polynomial Interpolation Method
by Joseph-Louis Lagrange
The French Academy of Sciences
1979

How to Share a Secret
by Dr. Adi Shamir
Turing Award Winner, Weizmann Institute and Massachusetts Institute of Technology
1991

Verifiable Secret Sharing Scheme
by Dr. Paul Feldman
MIT Computer Science & Artificial Intelligence Laboratory
1992

Non-Interactive and Information-Theoretic Secure Verifiable Secret Sharing
by Dr. Torben Pedersen
Aarhus University, Denmark
Discrete Logarithm Encryption
1976

New Directions in Cryptography
by Dr. Martin Hellman & Dr. Whitfield Diffie
Turing Award Winners, Stanford University
1978

Secure communications over insecure channels
by Dr. Ralph Merkle
University of California Berkeley & Georgia Institute of Technology
1985
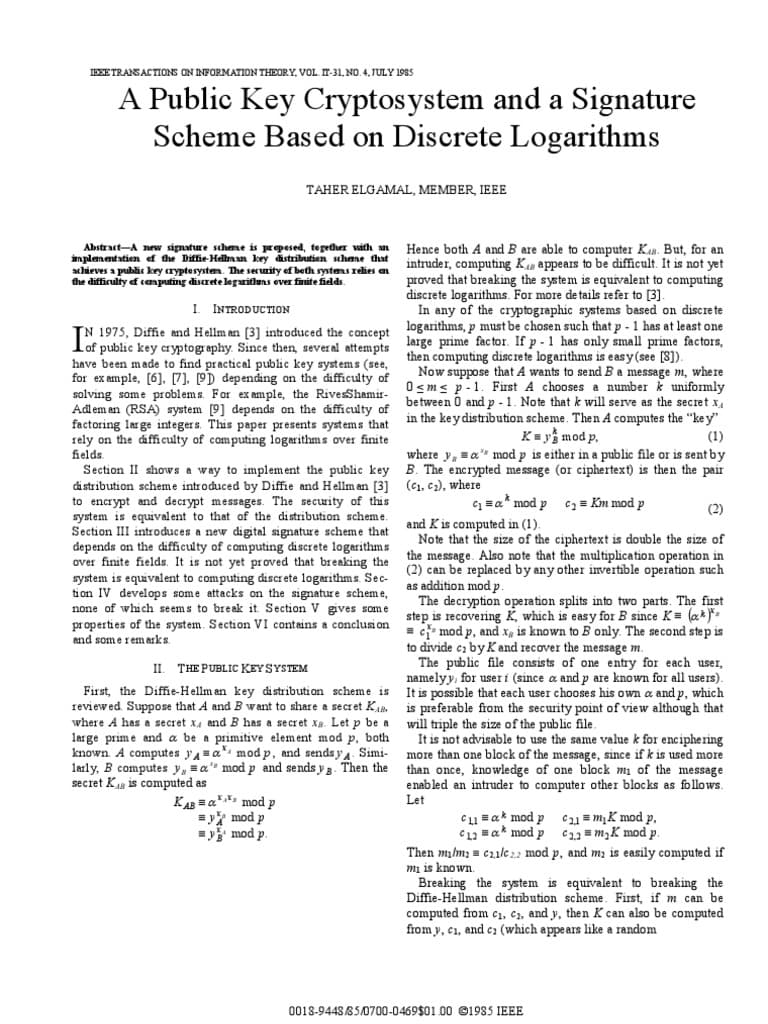
A public key cryptosystem and a signature scheme based on discrete logarithms
by Dr. Taher Elgamal
Stanford University
Anonymization Mixnet
1986

How To Prove Yourself: Practical Solutions to Identification and Signature Problems
by Dr. Amos Fiat & Dr. Adi Shamir
Tel Aviv University, Weizmann Institute of Science, and Massachusetts Institute of Technology
2001

A Verifiable Secret Shuffle and its Application to E-Voting
by Dr. Andrew Neff
Princeton University
Elliptic Curve Cryptography
1987

Speeding the Pollard and Elliptic Curve Methods of Factorization
by Dr. Peter L. Montgomery
University of California, Los Angeles
2006

Curve25519: new Diffie-Hellman speed records
by Dr. Daniel J. Bernstein
University of Illinois at Chicago, Eindhoven University of Technology
2018

Ristretto 255: Prime Order Groups
by Dr. Mike Hamburg et al.
Stanford University