




Only legitimately registered voters are allowed to vote, and only once per person.
A fair election requires that voters can freely choose without anyone learning how they voted.
For widely accepted results, vote totals must be independently auditable for accuracy.
There have already been digital systems in widespread use that offer each of these properties individually. Yet accomplishing all three at the same time has been unusually challenging.
Voter Registration
Election administrator collects list of all valid voters, via the same methods as currently used.
| Name | Mailing Address | Email Address | |||||
|---|---|---|---|---|---|---|---|
| Barton, Adam | ... | ... | |||||
| Green, Elissa | ... | ... | |||||
| Hauck, Erik | ... | ... | |||||
| Schuster, Brad | ... | ... | |||||
| Swift, Savannah | ... | ... | |||||
New
Ballot Finalized
The official ballot is finalized, as with traditional paper elections.
There can be multiple questions, as many as the election requires.
Privacy Protectors Registration
To give voters additional confidence that the election is run fairly, administrators have the option to add SIV “Privacy Protectors”.
These are like the observers in our existing paper elections, but SIV Privacy Protectors are vastly more powerful, because they use strong cryptography to ensure every vote is private and tamper-free.
After anonymization (Step 4), the Privacy Protectors work together to unlock the votes for tallying (Step 5).
Step 1: Invitation to Vote
Election administrator sends individualized invitations to all enrolled voters.
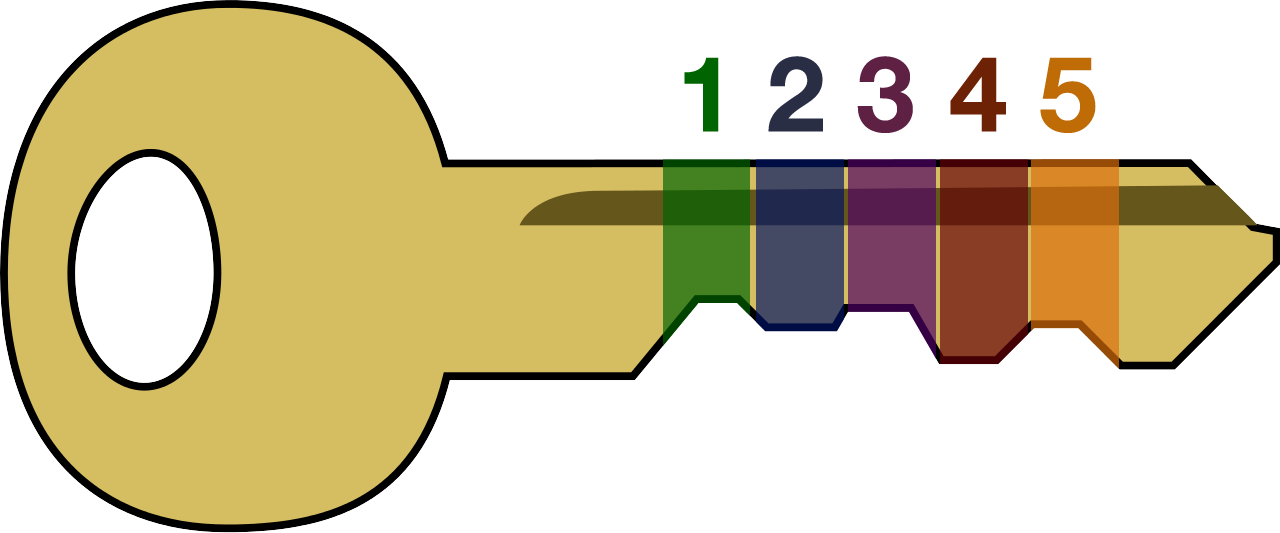
The purpose of this step is to get each voter their Voter Auth Token, highlighted in orange.
Key Properties of Voter Auth Tokens
Here we use an easy distribution channel — a simple email. But election administrators can offer other options, including 2-factor methods with drawn signatures, SMS, TOTP, or IP address geolocation.
Admins can even send Voter Auth Tokens via traditional postal mail. In other words, SIV can match the Voter Authentication requirements of existing processes, while upgrading the return ballot process to be faster, more accessible, and end-to-end verifiable.
See How does SIV ensure One Vote per Person? for more.
From: elections@local.gov
To: you@email.com
Subject: Your Vote Invitation
Voting for our next Mayor is now open.
Votes are accepted for the next 14 days.
Click here to securely cast your vote:
www.local.gov/vote?auth=d71f8698a3
This link is unique for you. Don't share it with anyone, or they'll be able to take your vote. (Help)
Step 2: Mark & Encrypt Your Vote
Voter fills out their ballot, which gets immediately encrypted.
SIV shows voters a simple point-and-click interface to fill out their ballot:
Who should be the next Mayor?
Verification #:
This Verification # will be publicly shown once votes are unlocked. It allows you to easily verify your vote was counted correctly, while protecting your privacy.
This unique value was generated on your own device. Don't share it with anyone.
DETAILED ENCRYPTION RECEIPT
Election: Demo Election
Election ID: 123
Voter Auth Token: d71f8698a3
---------
Submitted at: Wed Feb 25 2026 21:18:26 GMT+0000 (Coordinated Universal Time)
---------
Encryption Formula
https://en.wikipedia.org/wiki/ElGamal_encryption
in the Ristretto255 prime-order group derived from Curve25519
Encrypted = Encoded + (Recipient * randomizer)
Lock = (Generator * randomizer)
Encryption Public Key
Recipient: 2e4fc41d9e395a5b59e59eb8e01436b62cae94de8524539b3905dee8d2cfab4c
Generator: e2f2ae0a6abc4e71a884a961c500515f58e30b6aa582dd8db6a65945e08d2d76
---------
Verification #: 2153-9151-6236
Step 3: Submit Encrypted Vote
The voter sends their encrypted vote, with their Auth Token, to the election administrator.
{ auth: 'd71f8698a3', mayor_vote: }If it passes, the vote is added to a public list of all votes received so far.
{ auth: '7d20b493af', mayor_vote: { encrypted: 7e59b03d4d682aab7b0d7ae4c86cd6f012f74ebc457ee8c6456f826055edaa2b, lock: b63b8c0594ab6a8cd973fea58b7d0aac1c1f6dacf54cdbfa010de4b07cd35140 }
{ auth: '48bd4dea87', mayor_vote: { encrypted: b2ce1f37082c859ea1a8e585d018f3924bc211496fe4f0c5d9fc03863a15f90b, lock: d41b15a7246ec310ed06ed171e100c2d37681e2c66d3bcd40bd37de7ac17147c }
{ auth: '12bd9951ce', mayor_vote: { encrypted: 9cf2169ba7ef3df5001e19eb98a275c48be7bdbcd147eea4687eef94249ed418, lock: 4ea793ff158b9a94b19a06a12984a3aff1ba4e9fbc0b7823bcf4755f6071a327 }
{ auth: 'cab22f6ff2', mayor_vote: { encrypted: d044d879803011188cce241e140d7dfe444ecbe4aa0e02880333e03c6fdab470, lock: 38dba29dabc98b414da08c4ac3f5bc0fd0ea0283e3e2aa25641cb3cfd79bc774 }
{ auth: 'd71f8698a3', mayor_vote: undefined }
The voter is sent a confirmation that their encrypted vote has been received and accepted.
Because of the strong encryption, the election administrator still has no way to know how individual voters choose to vote.
From: elections@local.gov
To: you@email.com
Subject: Vote Confirmation
Your vote for mayor has been received. Thank you.
The final results will be posted at www.local.gov/election-results when the election closes.
Here is the encrypted vote you submitted:
{ auth: 'd71f8698a3', mayor_vote: }If you did not submit this ballot, click here to report a problem.
Step 4: Verifiable Shuffle
All the encrypted votes are then anonymized by the Privacy Protectors.
{ auth: '7d20b493af', mayor_vote: { encrypted: 7e59b03d4d682aab7b0d7ae4c86cd6f012f74ebc457ee8c6456f826055edaa2b, lock: b63b8c0594ab6a8cd973fea58b7d0aac1c1f6dacf54cdbfa010de4b07cd35140 } }
{ auth: '48bd4dea87', mayor_vote: { encrypted: b2ce1f37082c859ea1a8e585d018f3924bc211496fe4f0c5d9fc03863a15f90b, lock: d41b15a7246ec310ed06ed171e100c2d37681e2c66d3bcd40bd37de7ac17147c } }
{ auth: '12bd9951ce', mayor_vote: { encrypted: 9cf2169ba7ef3df5001e19eb98a275c48be7bdbcd147eea4687eef94249ed418, lock: 4ea793ff158b9a94b19a06a12984a3aff1ba4e9fbc0b7823bcf4755f6071a327 } }
{ auth: 'cab22f6ff2', mayor_vote: { encrypted: d044d879803011188cce241e140d7dfe444ecbe4aa0e02880333e03c6fdab470, lock: 38dba29dabc98b414da08c4ac3f5bc0fd0ea0283e3e2aa25641cb3cfd79bc774 } }
{ auth: 'd71f8698a3', mayor_vote: }
{ mayor_vote: { encrypted: 7e59b03d4d682aab7b0d7ae4c86cd6f012f74ebc457ee8c6456f826055edaa2b, lock: b63b8c0594ab6a8cd973fea58b7d0aac1c1f6dacf54cdbfa010de4b07cd35140 } }
{ mayor_vote: { encrypted: b2ce1f37082c859ea1a8e585d018f3924bc211496fe4f0c5d9fc03863a15f90b, lock: d41b15a7246ec310ed06ed171e100c2d37681e2c66d3bcd40bd37de7ac17147c } }
{ mayor_vote: { encrypted: 9cf2169ba7ef3df5001e19eb98a275c48be7bdbcd147eea4687eef94249ed418, lock: 4ea793ff158b9a94b19a06a12984a3aff1ba4e9fbc0b7823bcf4755f6071a327 } }
{ mayor_vote: { encrypted: d044d879803011188cce241e140d7dfe444ecbe4aa0e02880333e03c6fdab470, lock: 38dba29dabc98b414da08c4ac3f5bc0fd0ea0283e3e2aa25641cb3cfd79bc774 } }
{ mayor_vote: }
This randomizes the order of the votes, like mixing them up in a hat.
But this alone isn't enough to properly anonymize them, because the encrypted data — the outsides of our metaphorical locked safes — are still distinguishable. Any computer could quickly reconstruct the original list.
{mayor_vote: { encrypted: 7e59b03d4d682aab7b0d7ae4c86cd6f012f74ebc457ee8c6456f826055edaa2b, lock: b63b8c0594ab6a8cd973fea58b7d0aac1c1f6dacf54cdbfa010de4b07cd35140 } }
{mayor_vote: { encrypted: b2ce1f37082c859ea1a8e585d018f3924bc211496fe4f0c5d9fc03863a15f90b, lock: d41b15a7246ec310ed06ed171e100c2d37681e2c66d3bcd40bd37de7ac17147c } }
{mayor_vote: { encrypted: 9cf2169ba7ef3df5001e19eb98a275c48be7bdbcd147eea4687eef94249ed418, lock: 4ea793ff158b9a94b19a06a12984a3aff1ba4e9fbc0b7823bcf4755f6071a327 } }
{mayor_vote: { encrypted: d044d879803011188cce241e140d7dfe444ecbe4aa0e02880333e03c6fdab470, lock: 38dba29dabc98b414da08c4ac3f5bc0fd0ea0283e3e2aa25641cb3cfd79bc774 } }
{mayor_vote: { encrypted: 9cf2169ba7ef3df5001e19eb98a275c48be7bdbcd147eea4687eef94249ed418, lock: 4ea793ff158b9a94b19a06a12984a3aff1ba4e9fbc0b7823bcf4755f6071a327 } }
Now, the shuffled list is cryptographically mixed, with the original Auth Tokens unlinkable.
Their shuffled + re-encrypted list is now published publicly.
For strong cryptographic privacy, Privacy Protector #2 then repeats this same shuffle + re-encryption process, starting with the mixed list from Privacy Protector #1.
This way, all of the Privacy Protectors independently shuffle the encrypted votes, like multiple people shuffling a deck of cards, then handing it off to the next person.
This design creates multiple fail-safes. Even if some Privacy Protectors' devices are compromised, vote privacy can still be protected.




Step 5: Votes Unlocked & Tallied
The Privacy Protectors then work together to Unlock the final shuffled list.

Any voter can Search (Ctrl+F) to find their individual submission, via their Verification #, and see that their vote was counted correctly.
Anyone can independently tally the vote totals themselves.
Only submissions from authenticated voters were accepted, which can be verified with Risk-Limiting Audits after the election.
{ mayor_vote: 'Jane Kim', verification: '6401-3474-7848' }
{ mayor_vote: 'Mark Leno', verification: '4096-2282-7200' }
{ mayor_vote: 'Angela Alioto', verification: '7372-8261-8634' }
{ mayor_vote: 'Jane Kim', verification: '3648-6161-3732' }
{ mayor_vote: 'undefined', verification: '2153-9151-6236' }
We've now succeeded to run an election that's authenticated, private, & end-to-end verifiable.
For more information, see the Frequently Asked Questions page, or reach out to team@siv.org.